Fully translated + good linking
This commit is contained in:
@@ -53,7 +53,7 @@ Assume your service runs on port `3000` locally (`http://192.168.1.50:3000`), yo
|
||||
::alert{type="warning"}
|
||||
:::list{type="warning"}
|
||||
- __Warning:__ If you have multiple services to expose like `subdomain1.mydomain.com` and `subdomain2.mydomain.com`, your router cannot differentiate requests and forward to different ports.
|
||||
You must use a [Reverse Proxy](../../serveex/coeur/swag) to route traffic based on the request.
|
||||
You must use a [Reverse Proxy](../../serveex/core/swag) to route traffic based on the request.
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -55,7 +55,7 @@ So, if you want to point `mydomain.com` to your server, you can do it by adding
|
||||
- __Warning:__ If your server is hosted at home:
|
||||
:::
|
||||
- Your public IP is the one assigned to your home router. Make sure it's static, or configure [DDNS](https://aws.amazon.com/fr/what-is/dynamic-dns/).
|
||||
- Make sure you've [set up port 443 forwarding to your server's listening port](/generalites/nat).
|
||||
- Make sure you've [set up port 443 forwarding to your server's listening port](/general/nat).
|
||||
::
|
||||
|
||||
If you're adding a subdomain that should also point to your server, use a `CNAME` record pointing to `mydomain.com`.
|
||||
@@ -18,8 +18,8 @@ A big thanks to **Nipah** for sharing his infinite knowledge and, above all, for
|
||||
**Prerequisites:**
|
||||
:::list{type="primary"}
|
||||
- Have [an online VPS](https://www.it-connect.fr/les-serveurs-prives-virtuels-vps-pour-les-debutants/) or a local machine: ideally a mini PC (you can find N100 models for around €100), but it also works on a laptop or [a virtual machine](https://openclassrooms.com/fr/courses/2035806-virtualisez-votre-architecture-et-vos-environnements-de-travail/6313946-installez-virtualbox). The [Freebox Delta/Ultra offer virtual machines](https://next.ink/3493/machines-virtuelles-et-freebox-delta-comment-heberger-votre-premiere-page-web/).
|
||||
- Know how to configure [NAT rules on a router and assign DHCP leases](/generalites/nat)
|
||||
- Know how to configure the [DNS zone of a domain name](/generalites/dns)
|
||||
- Know how to configure [NAT rules on a router and assign DHCP leases](/general/nat)
|
||||
- Know how to configure the [DNS zone of a domain name](/general/dns)
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -38,28 +38,28 @@ The Core of the Server
|
||||
#title
|
||||
__Operating System__
|
||||
#description
|
||||
[Install and configure Debian 12](/serveex/coeur/installation)
|
||||
[Install and configure Debian 12](/serveex/core/installation)
|
||||
::
|
||||
|
||||
::card{icon=logos:docker-icon}
|
||||
#title
|
||||
__Container Engine__
|
||||
#description
|
||||
[Install Docker](/serveex/coeur/docker)
|
||||
[Install Docker](/serveex/core/docker)
|
||||
::
|
||||
|
||||
::card{icon=carbon:container-registry style="color: rgb(41, 194, 243);" }
|
||||
#title
|
||||
__Docker GUI__
|
||||
#description
|
||||
[Install and deploy Dockge](/serveex/coeur/docker#installer-dockge-pour-gérer-et-déployer-les-conteneurs)
|
||||
[Install and deploy Dockge](/serveex/core/docker#installer-dockge-pour-gérer-et-déployer-les-conteneurs)
|
||||
::
|
||||
|
||||
::card{icon=noto:globe-showing-americas}
|
||||
#title
|
||||
__Reverse Proxy__
|
||||
#description
|
||||
[Expose your services with SWAG](/serveex/coeur/swag)
|
||||
[Expose your services with SWAG](/serveex/core/swag)
|
||||
::
|
||||
::
|
||||
|
||||
@@ -272,5 +272,4 @@ Useful Applications
|
||||
- Homepage, to have all your services at a glance and access them easily
|
||||
- Mkdocs for your documentation
|
||||
- Docus, an alternative to Mkdocs
|
||||
- Speedtest Tracker to check your server's connection
|
||||
- UpSnap to remotely wake your machines
|
||||
|
||||
@@ -1,398 +0,0 @@
|
||||
---
|
||||
navigation: true
|
||||
title: SWAG
|
||||
main:
|
||||
fluid: false
|
||||
---
|
||||
:ellipsis{left=0px width=40rem top=10rem blur=140px}
|
||||
# SWAG
|
||||
|
||||
::alert{type="info"}
|
||||
🎯 __Objectifs :__
|
||||
- Installer Swag
|
||||
- Activer le SSL
|
||||
- Accéder au tableau de bord
|
||||
- Configurer le blocage régional
|
||||
- Exposer Dockge
|
||||
::
|
||||
|
||||
[Swag](https://docs.linuxserver.io/general/swag/) est le noyau de ce homelab. C'est un reverse proxy puissant qui permet d'exposer des services sur le net via un ou des noms de domaines, en se chargeant de l'émission des certificats SSL (pour garder des connexions chiffrées), du routage des requêtes et de la sécurisation des accès (par authent HTTP ou par SSO comme Authelia ou Authentik). Toute la doc nécessaire ce [situe ici](https://docs.linuxserver.io/general/swag).
|
||||
|
||||
::alert{type="warning"}
|
||||
:::list{type="warning"}
|
||||
- SWAG n'a pour utilité que l'exposition de vos services sur internet. C'est à dire, y accéder via une url publique du type `https://service.mondomaine.fr`. Si vous ne souhaitez pas exposer vos services et plutôt utiliser systématiquement un VPN pour vous connecter à vos services à distance, vous pouvez directement aller [par ici](/serveex/securite/wireguard).
|
||||
:::
|
||||
::
|
||||
|
||||
Ci-dessous, vous trouverez un exemple, exposant Dockge. Nous installerons SWAG, ainsi que le mod dbip servant à bloquer les connexions en fonction de la géoloc, ainsi que le mod dashboard qui permet de piloter le fonctionnement de swag, fail2ban et la géoloc.
|
||||
|
||||
**Principe d'un reverse proxy et application dans notre cas :**
|
||||
|
||||

|
||||
|
||||
## Installation
|
||||
---
|
||||
|
||||
::alert{type="info" icon="exclamation-circle"}
|
||||
:::list{type="info"}
|
||||
- Ce tutoriel part du principe que vous avez un nom de domaine qui pointe vers votre serveur, et que votre box a une règle NAT qui redirige le port `443` vers l'adresse IP et le port `443` de votre serveur. Le nom de domaine d'exemple sera `mondomaine.fr`.
|
||||
:::
|
||||
::
|
||||
|
||||
Plan des fichiers que nous allons modifier :
|
||||
|
||||
```console
|
||||
root
|
||||
└── docker
|
||||
└── swag
|
||||
├── config
|
||||
│ ├── dns-conf
|
||||
│ │ └── ovh.ini
|
||||
│ └── nginx
|
||||
│ ├── dbip.conf
|
||||
│ ├── nginx.conf
|
||||
│ └── proxy-confs
|
||||
│ └── dockge.subdomain.conf
|
||||
├── compose.yml
|
||||
└── .env
|
||||
```
|
||||
|
||||
Ouvrez Dockge dans votre navigateur, cliquez sur `compose`, nommez la stack `swag` et copiez la conf ci-dessous
|
||||
|
||||
``` yaml
|
||||
---
|
||||
services:
|
||||
swag:
|
||||
image: lscr.io/linuxserver/swag:latest
|
||||
container_name: swag
|
||||
cap_add:
|
||||
- NET_ADMIN
|
||||
env_file:
|
||||
- .env
|
||||
environment:
|
||||
- TZ=Europe/Paris
|
||||
- URL=${DOMAIN}
|
||||
- EXTRA_DOMAINS=${DOMAINS}
|
||||
- SUBDOMAINS=wildcard # couvre les sous-domaines
|
||||
- VALIDATION=dns
|
||||
- DNSPLUGIN=${PLUGIN}
|
||||
- EMAIL=${EMAIL}
|
||||
- DOCKER_MODS=linuxserver/mods:swag-dbip|linuxserver/mods:swag-dashboard|linuxserver/mods:swag-auto-reload
|
||||
volumes:
|
||||
- /docker/swag/config:/config
|
||||
ports:
|
||||
- 80:80
|
||||
- 443:443
|
||||
- 81:81 # Nécessaire pour le dashboard
|
||||
restart: unless-stopped
|
||||
networks:
|
||||
- swag
|
||||
|
||||
networks:
|
||||
swag:
|
||||
name: swag_default
|
||||
|
||||
```
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Astuce :__
|
||||
ajoutez le label de watchtower dans chaque conteneur afin d'automatiser les mises à jour
|
||||
|
||||
```yaml
|
||||
services:
|
||||
swag:
|
||||
#...
|
||||
labels:
|
||||
- com.centurylinklabs.watchtower.enable=true
|
||||
::
|
||||
|
||||
Puis dans le `.env` :
|
||||
|
||||
```properties
|
||||
DOMAIN=
|
||||
DOMAINS=
|
||||
EMAIL=
|
||||
PLUGIN=
|
||||
```
|
||||
|
||||
Remplissez comme suit
|
||||
|
||||
| Propriété | Valeur | Exemples |
|
||||
|--------------------------|---------------------------------------------------------------------------|-----------------------|
|
||||
| ` DOMAIN`{lang=properties} | Votre domaine (cela couvre aussi tous les sous-domaines) | `mondomaine.fr` |
|
||||
| ` DOMAINS`{lang=properties} | Vos éventuels autres domaines | `monsecondomaine.fr` |
|
||||
| ` EMAIL`{lang=properties} | Votre email, pour générer le certificat | `votre@email.fr` |
|
||||
| ` PLUGIN`{lang=properties} | Le plugin pour générer le certificat, lié à votre [fournisseur de zone DNS](https://docs.linuxserver.io/general/swag/) | `ovh`<br>`cloudflare` |
|
||||
|
||||
Ici nous partons du principe que votre zone DNS est chez OVH. Déployez la stack une premiere fois. Dans les logs vous verrez qu'il n'arrivera pas à créer de certificat SSL car le fichier ovh.ini renvoi une erreur. Arretez la stack.
|
||||
|
||||
En CLI, allez dans le dossier dns-conf et éditez le fichier `ovh.ini` :
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Astuce pour les allergiques au terminal :__
|
||||
vous pouvez utiliser [File Browser](/serveex/files/file-browser) pour naviguer dans vos fichier et éditer vos documents au lieu d'utiliser les commandes du terminal.
|
||||
::
|
||||
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/dns-conf/ovh.ini
|
||||
```
|
||||
|
||||
Voici ce qui s'affiche :
|
||||
|
||||
```properties
|
||||
# Instructions: https://github.com/certbot/certbot/blob/master/certbot-dns-ovh/certbot_dns_ovh/__init__.py#L20
|
||||
# Replace with your values
|
||||
dns_ovh_endpoint = ovh-eu
|
||||
dns_ovh_application_key =
|
||||
dns_ovh_application_secret =
|
||||
dns_ovh_consumer_key =
|
||||
```
|
||||
Authentifiez vous et créez [votre token ici](https://www.ovh.com/auth/?onsuccess=https%3A%2F%2Fwww.ovh.com%2Fauth%2Fapi%2FcreateToken).
|
||||
|
||||
Les permissions à configurer sont les suivantes :
|
||||
|
||||
* ``GET /domain/zone/*``
|
||||
* ``PUT /domain/zone/*``
|
||||
* ``POST /domain/zone/*``
|
||||
* ``DELETE /domain/zone/*``
|
||||
|
||||
Notez les 3 clés temporairement et renseignez le fichier `ovh.ini`. (avec vim, `i` pour passer en modif, `Echap` quand c'est fini, `:x` pour sauvegarder et quitter)
|
||||
|
||||
Sauvegardez et quittez le fichier.
|
||||
|
||||
Configurez aussi swag pour qu'il accède à DBIP, le module de gestion des accès par géolocalisation /Ouvrez le fichier nginx.conf
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/nginx.conf
|
||||
```
|
||||
|
||||
Et ajoutez la ligne suivante en dessous de la section `http` :
|
||||
|
||||
```nginx
|
||||
include /config/nginx/dbip.conf
|
||||
```
|
||||
|
||||
Relancez la stack dans Dockge, cette fois le certificat SSL est bien émis ! Vérifiez dans les logs que le serveur est bien ready.
|
||||
|
||||
## Dashboard
|
||||
---
|
||||
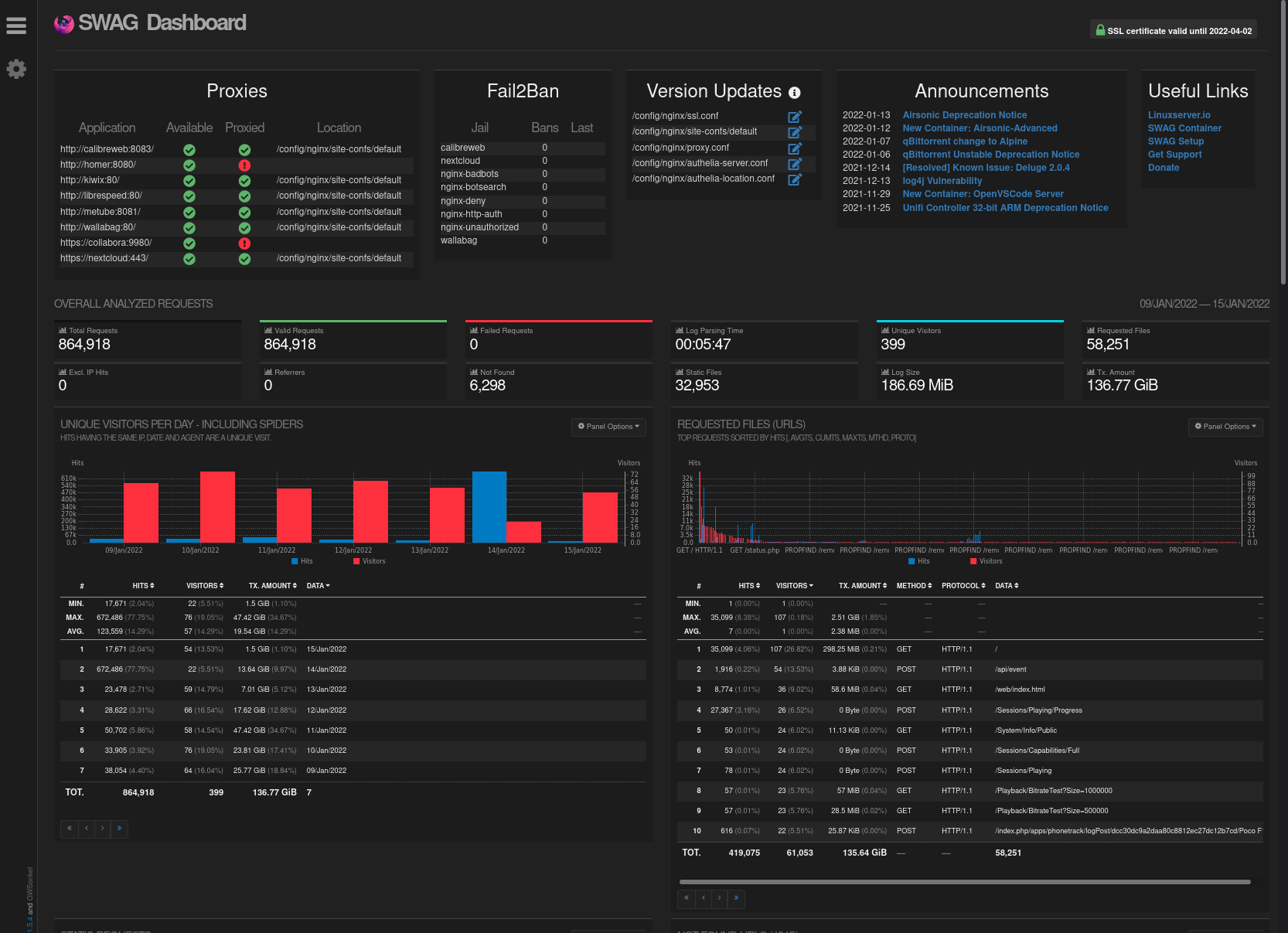
Accedez au dashboard via votre réseau local en tapant `http//ipdevotreserveur:81`
|
||||
A gauche, vous trouverez la liste des services actuellement "proxied" (aucun pour le moment). A droite, les IP bannies. En-dessous, une liste d'indicateurs. pour le détail, [c'est par ici](https://www.linuxserver.io/blog/introducing-swag-dashboard).
|
||||
|
||||
|
||||
|
||||
## DBIP
|
||||
---
|
||||
DBIP permet de bloquer les connexions en fonction des pays. Il s'appuie sur le fichier de config nommé `dbip.conf` dans `/docker/swag/config/nginx`. [Plus d'info ici](https://virtualize.link/secure/).
|
||||
|
||||
Dans cet exemple, nous allons le configurer pour bloquer une liste de pays connus pour etre à l'origine de la plupart des connexions malveillantes. Nous allons également configurer une variable au cas où nous souhaiterions permettre au réseau interne du serveur, au réseau local de votre box ainsi qu'à un éventuel vpn en 10.x.x.x de pouvoir accéder à vos services, mais pas directement à internet.
|
||||
|
||||
La configuration est activable ou désactivable pour chaque service qui sera proxied (voir exemple de Dockge plus bas).
|
||||
|
||||
Ouvrez `dbip.conf` :
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/dbip.conf
|
||||
```
|
||||
|
||||
Faites vos modifications ([voir documentation](https://github.com/linuxserver/docker-mods/tree/swag-dbip)), ou prenez l'exemple suivant:
|
||||
|
||||
```nginx
|
||||
geoip2 /config/geoip2db/dbip-country-lite.mmdb {
|
||||
auto_reload 1w;
|
||||
$geoip2_data_continent_code continent code;
|
||||
$geoip2_data_country_iso_code country iso_code;
|
||||
}
|
||||
|
||||
# Country Codes: https://en.wikipedia.org/wiki/ISO_3166-2
|
||||
|
||||
map $geoip2_data_country_iso_code $geo-whitelist {
|
||||
# default yes;
|
||||
# Example for whitelisting a country, comment out 'default yes;' above and uncomment 'default no;' and the whitelisted country below
|
||||
default no;
|
||||
FR yes;
|
||||
}
|
||||
|
||||
map $geoip2_data_country_iso_code $geo-blacklist {
|
||||
default yes;
|
||||
# Example for blacklisting a country, uncomment the blacklisted country below
|
||||
CN no; #China
|
||||
RU no; #Russia
|
||||
HK no; #Hong Kong
|
||||
IN no; #India
|
||||
IR no; #Iran
|
||||
VN no; #Vietnam
|
||||
TR no; #Turkey
|
||||
EG no; #Egypt
|
||||
MX no; #Mexico
|
||||
JP no; #Japan
|
||||
KR no; #South Korea
|
||||
KP no; #North Korea
|
||||
PE no; #Peru
|
||||
BR no; #Brazil
|
||||
UA no; #Ukraine
|
||||
ID no; #Indonesia
|
||||
TH no; #Thailand
|
||||
}
|
||||
|
||||
geo $lan-ip {
|
||||
default no;
|
||||
10.0.0.0/8 yes;
|
||||
172.16.0.0/12 yes;
|
||||
192.168.0.0/16 yes;
|
||||
127.0.0.1 yes;
|
||||
}
|
||||
```
|
||||
|
||||
Sauvegardez et quittez. Redémarrez la stack.
|
||||
|
||||
Dans les fichiers de conf des domaines (section suivante), vous pourrez activer ou désactiver la whitelist ou la blacklist ([voir documentation ici](https://www.forum-nas.fr/threads/tuto-installer-swag-en-docker-reverse-proxy.15057/)). Dans notre cas, la whitelist laisse uniquement passer les requêtes françaises. La blacklist laisse passer tout le monde sauf la liste de pays mentionnée. On utilisera donc la blacklist, sur ce modèle :
|
||||
|
||||
```nginx
|
||||
server {
|
||||
listen 443 ssl;
|
||||
listen [::]:443 ssl;
|
||||
|
||||
server_name some-app.*;
|
||||
include /config/nginx/ssl.conf;
|
||||
client_max_body_size 0;
|
||||
|
||||
if ($geo-blacklist = no) { return 404; }
|
||||
|
||||
location / {
|
||||
```
|
||||
|
||||
|
||||
## Exposer Dockge
|
||||
---
|
||||
::alert{type="info"}
|
||||
📋 __Prérequis :__ <br/></br>
|
||||
Nous partons du principe que vous avez créé dans votre [zone DNS](/generalites/dns) un sous domaine du type `dockge.mondomaine.fr` avec pour `CNAME` `mondomaine.fr` et [à moins que vous utilisiez Cloudflare Zero Trust](/serveex/securite/cloudflare), que vous avez déjà redirigé le port `443` de votre box vers le `443` de votre serveur dans [les règles NAT](/generalites/nat).
|
||||
::
|
||||
|
||||
Il s'agit maintenant d'exposer Dockge sur internet, afin de pouvoir y accéder et gérer vos conteneurs sans que vous soyez chez vous. Pour cela, nous partons du principe que vous avez configuré un sous domaine `dockge.mondomaine.fr` dans votre zone DNS dont le `CNAME` pointe sur `mondomaine.fr`.
|
||||
|
||||
::alert{type="warning"}
|
||||
:::list{type="warning"}
|
||||
- Dockge n'utilise pas d'authentification multifacteur. Exposer Dockge sur internet pourrait compromettre les machines auxquelles il est relié. Ne le faite que si vous utilisez un systeme d'authentification multifacteur comme [Authentik](/serveex/securite/authentik/). Sinon, n'exposez pas avec SWAG et utilisez plutôt un VPN comme [Wireguard](/serveex/securite/wireguard).
|
||||
:::
|
||||
::
|
||||
|
||||
Ouvrez le fichier dockge.subdomain.conf :
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/proxy-confs/dockge.subdomain.conf
|
||||
```
|
||||
|
||||
Paramétrez le comme tel :
|
||||
|
||||
```nginx
|
||||
## Version 2023/12/19
|
||||
|
||||
server {
|
||||
listen 443 ssl;
|
||||
listen [::]:443 ssl;
|
||||
|
||||
# indique que le sous-domaine doit être dirigé
|
||||
server_name dockge.*;
|
||||
|
||||
include /config/nginx/ssl.conf;
|
||||
|
||||
client_max_body_size 0;
|
||||
|
||||
#if ($lan-ip = yes) { set $geo-whitelist yes; }
|
||||
#if ($geo-whitelist = no) { return 404; }
|
||||
# indique que les pays dans la blacklist sont intedits
|
||||
if ($geo-blacklist = no) { return 404; }
|
||||
|
||||
# enable for ldap auth (requires ldap-location.conf in the location block)
|
||||
#include /config/nginx/ldap-server.conf;
|
||||
|
||||
# enable for Authelia (requires authelia-location.conf in the location block)
|
||||
#include /config/nginx/authelia-server.conf;
|
||||
|
||||
# enable for Authentik (requires authentik-location.conf in the location block)
|
||||
#include /config/nginx/authentik-server.conf;
|
||||
|
||||
location / {
|
||||
# enable the next two lines for http auth
|
||||
#auth_basic "Restricted";
|
||||
#auth_basic_user_file /config/nginx/.htpasswd;
|
||||
|
||||
# enable for ldap auth (requires ldap-server.conf in the server block)
|
||||
#include /config/nginx/ldap-location.conf;
|
||||
|
||||
# enable for Authelia (requires authelia-server.conf in the server block)
|
||||
#include /config/nginx/authelia-location.conf;
|
||||
|
||||
# enable for Authentik (requires authentik-server.conf in the server block)
|
||||
#include /config/nginx/authentik-location.conf;
|
||||
|
||||
include /config/nginx/proxy.conf;
|
||||
include /config/nginx/resolver.conf;
|
||||
|
||||
set $upstream_app dockge; # Nom du conteneur
|
||||
set $upstream_port 5001; # Port interne conteneur
|
||||
set $upstream_proto http;
|
||||
proxy_pass $upstream_proto://$upstream_app:$upstream_port;
|
||||
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
|
||||
Sauvegardez et quittez. La configuration va se mettre à jour en quelques secondes.
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- Par défaut, SWAG ne connait pas le nom "dockge". Pour qu'il puisse y accéder, vous devez rajouter le réseau de dockge dans le `compose.yml` de SWAG.
|
||||
:::
|
||||
::
|
||||
|
||||
Rendez-vous sur la stack de SWAG, puis cliquez sur `éditer`, et ajouter le réseau de dockge dans le fichier de conf sur ce modele (les champs `networks`) :
|
||||
|
||||
|
||||
```yaml
|
||||
services:
|
||||
swag:
|
||||
container_name: #...
|
||||
# ...
|
||||
networks: # Relie le conteneur au réseau custom
|
||||
- dockge # Nom du réseau déclaré dans la stack
|
||||
|
||||
networks: # Définit le réseau custom
|
||||
#...
|
||||
dockge: # Nom du réseau déclaré dans la stack
|
||||
name: dockge_default # Nom véritable du réseau externe
|
||||
external: true # Précise que c'est un réseau à rechercher en externe
|
||||
```
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- Ici nous partons du principe que le nom du réseau de dockge est `dockge_default`. Vous pouvez vérifier que la connexion est opérationnelle en visitant le dashboard de SWAG en tapant `http://ipduserveur:81`.
|
||||
:::
|
||||
::
|
||||
|
||||
Déployez à nouveau la stack de SWAG.
|
||||
|
||||
Patientez puis tapez `https://dockge.mondomaine.fr` dans votre navigateur, vous devriez être redirigé vers dockge. Vous pouvez vérifier le statut du service via le dashboard (depuis votre réseau local, http://ipdevotreserveur:81)
|
||||
|
||||
|
||||
## Exposer un autre service avec SWAG
|
||||
---
|
||||
Swag dispose de modeles pour la plupart des services connus, nommés `nomduservice.subdomain.conf.sample`. Il vous suffit de créer le sous-domaine dans votre zone DNS chez votre registrar (comme OVH par exemple), de le faire pointer sur votre domaine principale (via un enregistrement CNAME) et de copier en renommant `nomduservice.subdomain.conf.sample` en `nomduservice.subdomain.conf`.
|
||||
|
||||
```shell
|
||||
cd /docker/swag/config/proxy-confs
|
||||
sudo cp nomduservice.subdomain.conf.sample nomduservice.subdomain.conf
|
||||
```
|
||||
::alert{type="danger"}
|
||||
:::list{type="danger"}
|
||||
- __Si le sous domaine n'est pas redirigé correctement__
|
||||
:::
|
||||
- éditez le fichier et vérifiez notamment le nom du conteneur dans `set $upstream_app nomduconteneur;`{lang=nginx}
|
||||
|
||||
- vérifiez que vous avez bien ajouté le réseau du conteneur dans le `compose.yml` de SWAG.
|
||||
::
|
||||
|
||||
Vous pouvez aussi choisir le sous-domaine en changeant la variable `server_name votresousdomaine.*;`{lang=nginx} et en renommant le fichier `votresousdomaine.subdomain.conf`.
|
||||
@@ -60,7 +60,7 @@ Additionally:
|
||||
- [Firewalld](https://linuxcapable.com/how-to-install-firewalld-on-debian-linux/)
|
||||
|
||||
### Samba Sharing (Access a Remote Network Disk)
|
||||
- [Create and Access a Samba Share](/generalites/samba)
|
||||
- [Create and Access a Samba Share](/general/samba)
|
||||
|
||||
|
||||
### File Transfer via rsync
|
||||
379
content/3.serveex/2.core/3.swag.md
Normal file
379
content/3.serveex/2.core/3.swag.md
Normal file
@@ -0,0 +1,379 @@
|
||||
---
|
||||
navigation: true
|
||||
title: SWAG
|
||||
main:
|
||||
fluid: false
|
||||
---
|
||||
:ellipsis{left=0px width=40rem top=10rem blur=140px}
|
||||
# SWAG
|
||||
|
||||
::alert{type="info"}
|
||||
🎯 __Objectives:__
|
||||
- Install Swag
|
||||
- Enable SSL
|
||||
- Access the dashboard
|
||||
- Configure regional blocking
|
||||
- Expose Dockge
|
||||
::
|
||||
|
||||
[Swag](https://docs.linuxserver.io/general/swag/) is the core of this homelab. It’s a powerful reverse proxy that allows you to expose services on the internet using domain names, handling SSL certificate issuance (for encrypted connections), request routing, and access security (via HTTP auth or SSO like Authelia or Authentik). All the necessary documentation is [available here](https://docs.linuxserver.io/general/swag).
|
||||
|
||||
::alert{type="warning"}
|
||||
:::list{type="warning"}
|
||||
- SWAG is only useful for exposing your services to the internet—i.e., accessing them via a public URL like `https://service.mydomain.com`. If you don’t want to expose your services and prefer to always use a VPN to connect remotely, you can go [here instead](/serveex/securite/wireguard).
|
||||
:::
|
||||
::
|
||||
|
||||
Below is an example exposing Dockge. We will install SWAG along with the dbip mod for geolocation-based blocking, and the dashboard mod for managing swag, fail2ban, and geolocation.
|
||||
|
||||
**Reverse proxy principle and its application in our case:**
|
||||
|
||||

|
||||
|
||||
## Installation
|
||||
---
|
||||
|
||||
::alert{type="info" icon="exclamation-circle"}
|
||||
:::list{type="info"}
|
||||
- This tutorial assumes you have a domain name pointing to your server, and that your router has a NAT rule forwarding port `443` to your server's IP and port `443`. The example domain will be `mydomain.com`.
|
||||
:::
|
||||
::
|
||||
|
||||
File structure to be modified:
|
||||
|
||||
```console
|
||||
root
|
||||
└── docker
|
||||
└── swag
|
||||
├── config
|
||||
│ ├── dns-conf
|
||||
│ │ └── ovh.ini
|
||||
│ └── nginx
|
||||
│ ├── dbip.conf
|
||||
│ ├── nginx.conf
|
||||
│ └── proxy-confs
|
||||
│ └── dockge.subdomain.conf
|
||||
├── compose.yml
|
||||
└── .env
|
||||
```
|
||||
|
||||
Open Dockge in your browser, click on `compose`, name the stack `swag`, and copy the following config:
|
||||
|
||||
```yaml
|
||||
---
|
||||
services:
|
||||
swag:
|
||||
image: lscr.io/linuxserver/swag:latest
|
||||
container_name: swag
|
||||
cap_add:
|
||||
- NET_ADMIN
|
||||
env_file:
|
||||
- .env
|
||||
environment:
|
||||
- TZ=Europe/Paris
|
||||
- URL=${DOMAIN}
|
||||
- EXTRA_DOMAINS=${DOMAINS}
|
||||
- SUBDOMAINS=wildcard
|
||||
- VALIDATION=dns
|
||||
- DNSPLUGIN=${PLUGIN}
|
||||
- EMAIL=${EMAIL}
|
||||
- DOCKER_MODS=linuxserver/mods:swag-dbip|linuxserver/mods:swag-dashboard|linuxserver/mods:swag-auto-reload
|
||||
volumes:
|
||||
- /docker/swag/config:/config
|
||||
ports:
|
||||
- 80:80
|
||||
- 443:443
|
||||
- 81:81
|
||||
restart: unless-stopped
|
||||
networks:
|
||||
- swag
|
||||
|
||||
networks:
|
||||
swag:
|
||||
name: swag_default
|
||||
```
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__
|
||||
Add the watchtower label to each container to enable automatic updates
|
||||
|
||||
```yaml
|
||||
services:
|
||||
swag:
|
||||
#...
|
||||
labels:
|
||||
- com.centurylinklabs.watchtower.enable=true
|
||||
```
|
||||
::
|
||||
|
||||
Then in the `.env` file:
|
||||
|
||||
```properties
|
||||
DOMAIN=
|
||||
DOMAINS=
|
||||
EMAIL=
|
||||
PLUGIN=
|
||||
```
|
||||
|
||||
Fill out the variables as follows:
|
||||
|
||||
| Property | Value | Examples |
|
||||
|-------------------------|---------------------------------------------------------------------------|-----------------------|
|
||||
| `DOMAIN` | Your domain (covers all subdomains too) | `mydomain.com` |
|
||||
| `DOMAINS` | Any additional domains | `myseconddomain.com` |
|
||||
| `EMAIL` | Your email for generating the certificate | `your@email.com` |
|
||||
| `PLUGIN` | Plugin for certificate generation—depends on your [DNS provider](https://docs.linuxserver.io/general/swag/) | `ovh`<br>`cloudflare` |
|
||||
|
||||
Assuming your DNS zone is managed by OVH, deploy the stack once. The logs will show a failure in creating the SSL certificate due to a missing `ovh.ini` configuration. Stop the stack.
|
||||
|
||||
In CLI, go to the dns-conf folder and edit the `ovh.ini` file:
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip for terminal-shy users:__
|
||||
You can use [File Browser](/serveex/files/file-browser) to browse and edit files instead of using terminal commands.
|
||||
::
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/dns-conf/ovh.ini
|
||||
```
|
||||
|
||||
You should see:
|
||||
|
||||
```properties
|
||||
# Instructions: https://github.com/certbot/certbot/blob/master/certbot-dns-ovh/certbot_dns_ovh/__init__.py#L20
|
||||
# Replace with your values
|
||||
dns_ovh_endpoint = ovh-eu
|
||||
dns_ovh_application_key =
|
||||
dns_ovh_application_secret =
|
||||
dns_ovh_consumer_key =
|
||||
```
|
||||
|
||||
Authenticate and create [your token here](https://www.ovh.com/auth/?onsuccess=https%3A%2F%2Fwww.ovh.com%2Fauth%2Fapi%2FcreateToken).
|
||||
|
||||
Set the following permissions:
|
||||
|
||||
* `GET /domain/zone/*`
|
||||
* `PUT /domain/zone/*`
|
||||
* `POST /domain/zone/*`
|
||||
* `DELETE /domain/zone/*`
|
||||
|
||||
Note the 3 keys temporarily and enter them in `ovh.ini`. (In vim, press `i` to edit, `Esc` when done, `:x` to save and exit)
|
||||
|
||||
Save and exit the file.
|
||||
|
||||
Now configure swag to access DBIP, the geolocation-based access control module. Open the `nginx.conf` file:
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/nginx.conf
|
||||
```
|
||||
|
||||
Add the following line below the `http` section:
|
||||
|
||||
```nginx
|
||||
include /config/nginx/dbip.conf;
|
||||
```
|
||||
|
||||
Restart the stack in Dockge. This time, the SSL certificate should be successfully generated! Check the logs to confirm the server is ready.
|
||||
|
||||
## Dashboard
|
||||
---
|
||||
Access the dashboard locally by going to `http://yourserverip:81`
|
||||
On the left, you'll see a list of currently "proxied" services (none yet). On the right, the list of banned IPs. Below, various indicators. For more details, [click here](https://www.linuxserver.io/blog/introducing-swag-dashboard).
|
||||
|
||||

|
||||
|
||||
|
||||
## DBIP
|
||||
---
|
||||
DBIP allows you to block connections based on countries. It relies on the configuration file named `dbip.conf` located in `/docker/swag/config/nginx`. [More info here](https://virtualize.link/secure/).
|
||||
|
||||
In this example, we’ll configure it to block a list of countries known to be the source of most malicious traffic. We’ll also configure a variable to allow internal server traffic, your box’s local network, and a potential VPN in the 10.x.x.x range to access your services — but not the open internet.
|
||||
|
||||
This configuration can be enabled or disabled per service (see the Dockge example below).
|
||||
|
||||
Open `dbip.conf`:
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/dbip.conf
|
||||
```
|
||||
|
||||
Make your changes ([see documentation](https://github.com/linuxserver/docker-mods/tree/swag-dbip)), or use the following example:
|
||||
|
||||
```nginx
|
||||
geoip2 /config/geoip2db/dbip-country-lite.mmdb {
|
||||
auto_reload 1w;
|
||||
$geoip2_data_continent_code continent code;
|
||||
$geoip2_data_country_iso_code country iso_code;
|
||||
}
|
||||
|
||||
# Country Codes: https://en.wikipedia.org/wiki/ISO_3166-2
|
||||
|
||||
map $geoip2_data_country_iso_code $geo-whitelist {
|
||||
default no;
|
||||
FR yes;
|
||||
}
|
||||
|
||||
map $geoip2_data_country_iso_code $geo-blacklist {
|
||||
default yes;
|
||||
CN no; #China
|
||||
RU no; #Russia
|
||||
HK no; #Hong Kong
|
||||
IN no; #India
|
||||
IR no; #Iran
|
||||
VN no; #Vietnam
|
||||
TR no; #Turkey
|
||||
EG no; #Egypt
|
||||
MX no; #Mexico
|
||||
JP no; #Japan
|
||||
KR no; #South Korea
|
||||
KP no; #North Korea
|
||||
PE no; #Peru
|
||||
BR no; #Brazil
|
||||
UA no; #Ukraine
|
||||
ID no; #Indonesia
|
||||
TH no; #Thailand
|
||||
}
|
||||
|
||||
geo $lan-ip {
|
||||
default no;
|
||||
10.0.0.0/8 yes;
|
||||
172.16.0.0/12 yes;
|
||||
192.168.0.0/16 yes;
|
||||
127.0.0.1 yes;
|
||||
}
|
||||
```
|
||||
|
||||
Save and close the file. Restart the stack.
|
||||
|
||||
In the domain config files (see next section), you can enable or disable the whitelist or blacklist ([see documentation here](https://www.forum-nas.fr/threads/tuto-installer-swag-en-docker-reverse-proxy.15057/)). In our case, the whitelist allows only French requests. The blacklist blocks only the listed countries. We'll use the blacklist, like so:
|
||||
|
||||
```nginx
|
||||
server {
|
||||
listen 443 ssl;
|
||||
listen [::]:443 ssl;
|
||||
|
||||
server_name some-app.*;
|
||||
include /config/nginx/ssl.conf;
|
||||
client_max_body_size 0;
|
||||
|
||||
if ($geo-blacklist = no) { return 404; }
|
||||
|
||||
location / {
|
||||
```
|
||||
|
||||
## Exposing Dockge
|
||||
---
|
||||
::alert{type="info"}
|
||||
📋 __Prerequisite:__ <br/><br/>
|
||||
We assume that you have created a subdomain like `dockge.mydomain.com` in your [DNS zone](/general/dns), with a `CNAME` pointing to `mydomain.com` and — unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare) — that you've forwarded port `443` from your router to the server's `443` in [your NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
Now it's time to expose Dockge on the internet so you can access and manage your containers remotely. We assume you've set up the subdomain `dockge.mydomain.com` with a `CNAME` pointing to `mydomain.com`.
|
||||
|
||||
::alert{type="warning"}
|
||||
:::list{type="warning"}
|
||||
- Dockge does not support multi-factor authentication. Exposing it online could compromise all connected machines. Only do this if you're using an MFA solution like [Authentik](/serveex/securite/authentik/). Otherwise, don’t expose it with SWAG — use a VPN like [Wireguard](/serveex/securite/wireguard) instead.
|
||||
:::
|
||||
::
|
||||
|
||||
Open the `dockge.subdomain.conf` file:
|
||||
|
||||
```shell
|
||||
sudo vi /docker/swag/config/nginx/proxy-confs/dockge.subdomain.conf
|
||||
```
|
||||
|
||||
Configure it like this:
|
||||
|
||||
```nginx
|
||||
## Version 2023/12/19
|
||||
|
||||
server {
|
||||
listen 443 ssl;
|
||||
listen [::]:443 ssl;
|
||||
|
||||
server_name dockge.*; # define the subdomain to redirect
|
||||
|
||||
include /config/nginx/ssl.conf;
|
||||
|
||||
client_max_body_size 0;
|
||||
|
||||
#if ($lan-ip = yes) { set $geo-whitelist yes; }
|
||||
#if ($geo-whitelist = no) { return 404; }
|
||||
if ($geo-blacklist = no) { return 404; } # all countries un blacklist are forbidden
|
||||
|
||||
#include /config/nginx/ldap-server.conf;
|
||||
#include /config/nginx/authelia-server.conf;
|
||||
#include /config/nginx/authentik-server.conf;
|
||||
|
||||
location / {
|
||||
#auth_basic "Restricted";
|
||||
#auth_basic_user_file /config/nginx/.htpasswd;
|
||||
|
||||
#include /config/nginx/ldap-location.conf;
|
||||
#include /config/nginx/authelia-location.conf;
|
||||
#include /config/nginx/authentik-location.conf;
|
||||
|
||||
include /config/nginx/proxy.conf;
|
||||
include /config/nginx/resolver.conf;
|
||||
|
||||
set $upstream_app dockge; # container name
|
||||
set $upstream_port 5001; # internal container port (not exposed port)
|
||||
set $upstream_proto http;
|
||||
proxy_pass $upstream_proto://$upstream_app:$upstream_port;
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
Save and exit. The configuration will update within a few seconds.
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- By default, SWAG doesn’t recognize the name "dockge". You’ll need to add Dockge’s network to SWAG’s `compose.yml`.
|
||||
:::
|
||||
::
|
||||
|
||||
Go to the SWAG stack, click `edit`, and modify the config file like this (note the `networks` section):
|
||||
|
||||
```yaml
|
||||
services:
|
||||
swag:
|
||||
container_name: #...
|
||||
# ...
|
||||
networks: # Link the container to the custom network
|
||||
- dockge # Network name as defined in the stack
|
||||
|
||||
networks: # Define the custom network
|
||||
# ...
|
||||
dockge: # Network name as defined in the stack
|
||||
name: dockge_default # True external network name
|
||||
external: true
|
||||
```
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- We assume the Dockge network is named `dockge_default`. You can verify the setup works by checking the SWAG dashboard at `http://yourserverip:81`.
|
||||
:::
|
||||
::
|
||||
|
||||
Redeploy the SWAG stack.
|
||||
|
||||
Wait a moment, then visit `https://dockge.mydomain.com` in your browser — you should be redirected to Dockge. You can also check the service status from the dashboard (`http://yourserverip:81` on your local network).
|
||||
|
||||
## Exposing Another Service with SWAG
|
||||
---
|
||||
SWAG includes templates for most known services, named `servicename.subdomain.conf.sample`. Just create the subdomain in your registrar's DNS zone (like OVH), point it to your main domain via a CNAME, then copy and rename the sample file:
|
||||
|
||||
```shell
|
||||
cd /docker/swag/config/proxy-confs
|
||||
sudo cp servicename.subdomain.conf.sample servicename.subdomain.conf
|
||||
```
|
||||
|
||||
::alert{type="danger"}
|
||||
:::list{type="danger"}
|
||||
- __If the subdomain is not redirected properly__
|
||||
:::
|
||||
- Open the file and verify the container name in `set $upstream_app containername;`{lang=nginx}
|
||||
- Make sure you added the container's network in SWAG’s `compose.yml`
|
||||
::
|
||||
|
||||
You can also customize the subdomain by editing `server_name yoursubdomain.*;`{lang=nginx} and renaming the file to `yoursubdomain.subdomain.conf`.
|
||||
@@ -197,7 +197,7 @@ To use Authentik outside your local network, you must expose it.
|
||||
|
||||
::alert{type="info"}
|
||||
📋 __Prerequisites:__ <br/><br/>
|
||||
We assume you have already created a subdomain like `auth.mydomain.com` in your [DNS zone](/generalites/dns), with a CNAME pointing to `mydomain.com`. Also, unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare), you must have already forwarded port `443` from your router to port `443` of your server in your [NAT rules](/generalites/nat).
|
||||
We assume you have already created a subdomain like `auth.mydomain.com` in your [DNS zone](/general/dns), with a CNAME pointing to `mydomain.com`. Also, unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare), you must have already forwarded port `443` from your router to port `443` of your server in your [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
Open the `authentik-server.conf` file:
|
||||
@@ -363,14 +363,14 @@ Your new architecture looks like this:
|
||||
|
||||
## Protecting a Remote Server Service
|
||||
---
|
||||
For a [native application](/serveex/securite/authentik#protéger-une-app-native) (via OAuth 2.0 or other), nothing changes.
|
||||
For a [native application](/serveex/securite/authentik/#protecting-a-native-app) (via OAuth 2.0 or other), nothing changes.
|
||||
|
||||
For a non-native app behind a reverse proxy, you must deploy an __Outpost__. An Outpost is a container acting as a local proxy — it's the target of your app's auth requests and the only one authorized to communicate with your Authentik API.
|
||||
|
||||
::alert{type="info"}
|
||||
Prerequisites:
|
||||
- Install [Docker](/serveex/coeur/docker) on the remote server hosting the service.
|
||||
- If the app has no native integration, use a compatible reverse proxy. We will use [SWAG](/serveex/coeur/swag) here.
|
||||
- Install [Docker](/serveex/core/docker) on the remote server hosting the service.
|
||||
- If the app has no native integration, use a compatible reverse proxy. We will use [SWAG](/serveex/core/swag) here.
|
||||
::
|
||||
|
||||
This container will forward requests to your main [Authentik](/serveex/securite/authentik#authentik) instance over the internet (or your local network). The server will perform checks and respond to the Outpost, which will allow or block access accordingly.
|
||||
@@ -379,7 +379,7 @@ This container will forward requests to your main [Authentik](/serveex/securite/
|
||||
|
||||
### Configuring Authentik
|
||||
|
||||
Create your [providers and applications](/serveex/securite/authentik#protéger-une-app-native) as shown earlier.
|
||||
Create your [providers and applications](/serveex/securite/authentik/#protecting-a-native-app) as shown earlier.
|
||||
|
||||
Then, in the admin panel, go to _Applications > Outposts_, and create a new outpost.
|
||||
|
||||
@@ -413,11 +413,11 @@ On the list of created outposts, locate the new one and click _Show details_ at
|
||||
|
||||
### Configuring the Remote Machine
|
||||
|
||||
We assume you’ve already installed [Docker](/serveex/coeur/docker) and [SWAG](/serveex/coeur/swag) on this remote machine.
|
||||
We assume you’ve already installed [Docker](/serveex/core/docker) and [SWAG](/serveex/core/swag) on this remote machine.
|
||||
|
||||
On your remote machine, use [Dockge](/serveex/coeur/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs) to create a stack named `authentik-outpost`.
|
||||
On your remote machine, use [Dockge](/serveex/core/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs) to create a stack named `authentik-outpost`.
|
||||
|
||||
If you haven’t installed [Dockge](/serveex/coeur/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs), create a folder `/docker/authentik-outpost`, or directly via command line:
|
||||
If you haven’t installed [Dockge](/serveex/core/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs), create a folder `/docker/authentik-outpost`, or directly via command line:
|
||||
|
||||
```shell
|
||||
sudo mkdir -P /docker/authentik-outpost
|
||||
@@ -486,7 +486,7 @@ Press `Esc`, then type `:x` and press `Enter` to save and exit.
|
||||
:::
|
||||
::
|
||||
|
||||
If using [Dockge](/serveex/coeur/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs), restart SWAG.
|
||||
If using [Dockge](/serveex/core/docker/#installer-dockge-pour-gérer-et-déployer-les-conteneurs), restart SWAG.
|
||||
|
||||
Otherwise, via terminal:
|
||||
|
||||
@@ -547,7 +547,7 @@ proxy_pass http://$upstream_authentik:9000;
|
||||
|
||||
Save and exit with `Esc`, then `:x` and `Enter`.
|
||||
|
||||
Then configure the applications to protect as you did on your main server, whether they are [native](/serveex/securite/authentik#protéger-une-app-native) or protected via [reverse proxy](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
Then configure the applications to protect as you did on your main server, whether they are [native](/serveex/securite/authentik/#protecting-a-native-app) or protected via [reverse proxy](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
|
||||
## Migrating an Authentik Database
|
||||
---
|
||||
|
||||
@@ -21,7 +21,7 @@ main:
|
||||
---
|
||||
The _Zero Trust_ architecture is the practice of designing systems based on the principle of __"never trust, always verify"__, as opposed to the traditional principle of __"trust, but verify"__. This concept has become increasingly popular recently due to the growing number of attacks targeting user data. It’s a broad concept, but we’ll focus on how to apply _Zero Trust_ to the web services we host.
|
||||
|
||||
_Cloudflare tunnels_ offer a simple way to implement _Zero Trust_, using [SWAG](/serveex/coeur/swag) and [Authentik](/serveex/securite/authentik).
|
||||
_Cloudflare tunnels_ offer a simple way to implement _Zero Trust_, using [SWAG](/serveex/core/swag) and [Authentik](/serveex/securite/authentik).
|
||||
|
||||
Simply put, Cloudflare Tunnels allow you to:
|
||||
|
||||
@@ -46,7 +46,7 @@ Here we’ll explain how to integrate SWAG with Cloudflare tunnels.
|
||||
---
|
||||
### DNS Zone
|
||||
|
||||
First, you need to set Cloudflare as your [DNS zone](/generalites/dns) manager. If you bought your domain from Cloudflare, that’s already done. Otherwise, check with your registrar how to add external DNS servers. Cloudflare provides [step-by-step documentation](https://developers.cloudflare.com/dns/zone-setups/full-setup/setup/) on how to configure a DNS Zone, whether your domain is external or registered with Cloudflare.
|
||||
First, you need to set Cloudflare as your [DNS zone](/general/dns) manager. If you bought your domain from Cloudflare, that’s already done. Otherwise, check with your registrar how to add external DNS servers. Cloudflare provides [step-by-step documentation](https://developers.cloudflare.com/dns/zone-setups/full-setup/setup/) on how to configure a DNS Zone, whether your domain is external or registered with Cloudflare.
|
||||
|
||||
If you only have one server to protect behind Cloudflare, you can delete all existing DNS records. By default, your domain and all its subdomains will be redirected to the tunnel.
|
||||
|
||||
@@ -214,10 +214,10 @@ TUNNEL_PW=
|
||||
|
||||
Once done, deploy the stack. Check the logs—you should reach `server ready`.
|
||||
|
||||
Then confirm your tunnel appears under _Networks > Tunnels_ in [Cloudflare Zero Trust](https://one.dash.cloudflare.com/). By default, all subdomains will be routed through the tunnel—no need to define them [in your DNS zone](/generalites/dns).
|
||||
Then confirm your tunnel appears under _Networks > Tunnels_ in [Cloudflare Zero Trust](https://one.dash.cloudflare.com/). By default, all subdomains will be routed through the tunnel—no need to define them [in your DNS zone](/general/dns).
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__ If you want to expose a service without a tunnel, just define an A record [in your DNS zone](/generalites/dns). If resolution fails, disable the proxy function for that record—e.g., for `sub.mondomaine.fr`.
|
||||
✨ __Tip:__ If you want to expose a service without a tunnel, just define an A record [in your DNS zone](/general/dns). If resolution fails, disable the proxy function for that record—e.g., for `sub.mondomaine.fr`.
|
||||

|
||||
::
|
||||
|
||||
|
||||
@@ -69,7 +69,7 @@ You can now access the tool via `http://yourserverip:3200`.
|
||||
::alert{type="info"}
|
||||
📋 __Before you begin:__
|
||||
<br/><br/>
|
||||
We assume you have the subdomain `stats.mydomain.com` with a `CNAME` pointing to `mydomain.com` in your [DNS zone](/generalites/dns). And of course, [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` of your router should point to port `443` of your server via [NAT rules](/generalites/nat).
|
||||
We assume you have the subdomain `stats.mydomain.com` with a `CNAME` pointing to `mydomain.com` in your [DNS zone](/general/dns). And of course, [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` of your router should point to port `443` of your server via [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
::alert{type="warning"}
|
||||
@@ -178,7 +178,7 @@ You can protect this app with Authentik by opening `stats.subdomain.conf` and un
|
||||
`include /config/nginx/authentik-server.conf;`
|
||||
and
|
||||
`include /config/nginx/authentik-location.conf;`.
|
||||
Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy). If you want the public stats page to be accessible without authentication:
|
||||
Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy). If you want the public stats page to be accessible without authentication:
|
||||
|
||||
- Edit the Uptime-Kuma provider
|
||||
- In *Advanced Protocol Settings > Authenticated Paths*, enter:
|
||||
|
||||
@@ -81,7 +81,7 @@ You may want to access Dozzle remotely and on all your devices. To do so, we’l
|
||||
::alert{type="info"}
|
||||
📋 __Before you begin:__
|
||||
<br/><br/>
|
||||
We assume you have created a subdomain like `dozzle.mydomain.com` in your [DNS zone](/generalites/dns) with a `CNAME` pointing to `mydomain.com` and that, [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), you’ve redirected port `443` from your router to port `443` on your server in your [NAT rules](/generalites/nat).
|
||||
We assume you have created a subdomain like `dozzle.mydomain.com` in your [DNS zone](/general/dns) with a `CNAME` pointing to `mydomain.com` and that, [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), you’ve redirected port `443` from your router to port `443` on your server in your [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
Go to Dockge and edit the SWAG compose file to add Dozzle’s network:
|
||||
@@ -177,5 +177,5 @@ Press `Esc`, then save and exit by typing `:x` and pressing `Enter`.
|
||||
And there you go, Dozzle is now exposed!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ You can protect this app with Authentik by opening `dozzle.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and a provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ You can protect this app with Authentik by opening `dozzle.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and a provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
@@ -91,7 +91,7 @@ Deploy the container and go to `http://yourserverip:3225`. Log in with the accou
|
||||
---
|
||||
::alert{type="info"}
|
||||
📋 **Prerequisites:**
|
||||
We assume that you've already created a subdomain like `speedtest.yourdomain.com` in your [DNS zone](/generalites/dns) with a `CNAME` pointing to `yourdomain.com`, and [unless you’re using Cloudflare Zero Trust](/serveex/securite/cloudflare), you've also forwarded port `443` from your router to port `443` of your server in your [NAT rules](/generalites/nat).
|
||||
We assume that you've already created a subdomain like `speedtest.yourdomain.com` in your [DNS zone](/general/dns) with a `CNAME` pointing to `yourdomain.com`, and [unless you’re using Cloudflare Zero Trust](/serveex/securite/cloudflare), you've also forwarded port `443` from your router to port `443` of your server in your [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
Now we want to expose Speedtest Tracker to the internet so you can access it remotely. We assume you've set up the DNS `CNAME` for `speedtest.yourdomain.com` pointing to `yourdomain.com`.
|
||||
@@ -192,5 +192,5 @@ Wait a moment, then visit `https://speedtest.yourdomain.com` in your browser —
|
||||
::alert{type="success"}
|
||||
✨ You can protect this app with Authentik by opening `speedtest.subdomain.conf` and uncommenting
|
||||
`include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`.
|
||||
Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
@@ -157,7 +157,7 @@ If you want to access Beszel remotely from all your devices, expose it using Swa
|
||||
::alert{type="info"}
|
||||
📋 __Prerequisite:__
|
||||
<br/><br/>
|
||||
You must have created a DNS subdomain like `beszel.mydomain.com` with a `CNAME` pointing to `mydomain.com`, and—unless you're using Cloudflare Zero Trust—you must have forwarded port `443` on your router to your server’s `443` port via [NAT rules](/generalites/nat).
|
||||
You must have created a DNS subdomain like `beszel.mydomain.com` with a `CNAME` pointing to `mydomain.com`, and—unless you're using Cloudflare Zero Trust—you must have forwarded port `443` on your router to your server’s `443` port via [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
In Dockge, edit Swag's compose file and add Beszel’s network:
|
||||
@@ -247,5 +247,5 @@ Press `Esc`, type `:x`, and hit `Enter` to save and exit.
|
||||
That’s it—Beszel is now exposed!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ You can protect this app with Authentik by opening `beszel.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ You can protect this app with Authentik by opening `beszel.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
|
||||
@@ -94,7 +94,7 @@ You may want to access it remotely from all your devices. To do so, we'll expose
|
||||
::alert{type="info"}
|
||||
📋 __Beforehand:__
|
||||
<br/><br/>
|
||||
We assume you've created a subdomain in your [DNS zone](/generalites/dns), such as `upsnap.yourdomain.com` with a `CNAME` to `yourdomain.com`. Also, unless you're using Cloudflare Zero Trust, you should have already forwarded port `443` from your router to port `443` on your server in your [NAT rules](/generalites/nat).
|
||||
We assume you've created a subdomain in your [DNS zone](/general/dns), such as `upsnap.yourdomain.com` with a `CNAME` to `yourdomain.com`. Also, unless you're using Cloudflare Zero Trust, you should have already forwarded port `443` from your router to port `443` on your server in your [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
Go to Dockge, and edit the SWAG compose by adding the UpSnap network:
|
||||
@@ -190,5 +190,5 @@ Press `Escape`, then save and exit by typing `:x` and pressing `Enter`.
|
||||
And that’s it — you’ve exposed UpSnap!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ You can protect this app with Authentik by opening `upsnap.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ You can protect this app with Authentik by opening `upsnap.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
|
||||
@@ -144,7 +144,7 @@ Then go to the _Remote Access_ section and manually select a port (we’ll use `
|
||||
|
||||

|
||||
|
||||
- On your router, forward TCP port `1234` to port `32400` for your server’s IP using [NAT rules](/generalites/nat).
|
||||
- On your router, forward TCP port `1234` to port `32400` for your server’s IP using [NAT rules](/general/nat).
|
||||
- Once done, return to Plex to verify that remote access is functional.
|
||||
|
||||
::alert{type="danger"}
|
||||
@@ -163,7 +163,7 @@ Simply add your media to `/media/movies` and `/media/tvseries` on your server. Y
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- If your media is stored on a network disk (e.g. NAS or external hard drive over the network), refer to the [Samba mount guide](/generalites/samba) so Plex can access it.
|
||||
- If your media is stored on a network disk (e.g. NAS or external hard drive over the network), refer to the [Samba mount guide](/general/samba) so Plex can access it.
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -175,7 +175,7 @@ However, you may want to expose Tautulli so you can view stats from a simple URL
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- We assume you have the subdomain `tautulli.mydomain.com` with a `CNAME` pointing to `mydomain.com` in your [DNS zone](/generalites/dns). And of course, [unless you use Cloudflare Zero Trust](/serveex/securite/cloudflare), your box's port `443` must be forwarded to your server's port `443` in [NAT rules](/generalites/nat).
|
||||
- We assume you have the subdomain `tautulli.mydomain.com` with a `CNAME` pointing to `mydomain.com` in your [DNS zone](/general/dns). And of course, [unless you use Cloudflare Zero Trust](/serveex/securite/cloudflare), your box's port `443` must be forwarded to your server's port `443` in [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -298,21 +298,7 @@ server {
|
||||
```
|
||||
|
||||
::alert{type="success"}
|
||||
✨ Vous pouvez protéger cette app avec Authentik en retirant les `#` devant `include /config/nginx/authentik-server.conf;`{lang=nginx} et `include /config/nginx/authentik-location.conf;`{lang=nginx}. N'oubliez pas de [créer une application et un fournisseur dans Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
::
|
||||
|
||||
Appuyez sur `Echap` puis sauvegardez et quittez en tappant `:x`
|
||||
|
||||
Patientez quelques minutes puis tapez dans votre navigateur `http://tautulli.mondomaine.fr`.
|
||||
|
||||
::alert{type="danger"}
|
||||
:::list{type="danger"}
|
||||
- __En cas d'échec :__ vérifiez les règles de votre pare-feu.
|
||||
:::
|
||||
::
|
||||
|
||||
::alert{type="success"}
|
||||
✨ You can protect this app with Authentik by removing the `#` before `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ You can protect this app with Authentik by removing the `#` before `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
|
||||
Press `Esc` then save and quit by typing `:x`
|
||||
|
||||
@@ -218,7 +218,7 @@ To start downloads from outside your home, without a VPN, you can expose the Qbi
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- We assume you have the subdomain `seedbox.mydomain.com` with a `CNAME` pointing to `mydomain.com` in [DNS zone](/generalites/dns). And that port `443` on your router is forwarded to your server in [NAT rules](/generalites/nat), unless you’re using Cloudflare Zero Trust.
|
||||
- We assume you have the subdomain `seedbox.mydomain.com` with a `CNAME` pointing to `mydomain.com` in [DNS zone](/general/dns). And that port `443` on your router is forwarded to your server in [NAT rules](/general/nat), unless you’re using Cloudflare Zero Trust.
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -312,7 +312,7 @@ server {
|
||||
```
|
||||
|
||||
::alert{type="success"}
|
||||
✨ You can secure this app with Authentik by uncommenting the `authentik-server.conf` and `authentik-location.conf` lines. Don’t forget to [create an app and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ You can secure this app with Authentik by uncommenting the `authentik-server.conf` and `authentik-location.conf` lines. Don’t forget to [create an app and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
|
||||
Press `Esc`, type `:x` to save and quit.
|
||||
|
||||
@@ -385,7 +385,7 @@ It can be useful to expose Overseerr if you want to send requests from outside y
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- We assume you have the subdomain `films.mydomain.com` with a `CNAME` pointing to `films.fr` in your [DNS zone](/generalites/dns). And that [unless you’re using Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` on your router is forwarded to port `443` on your server via [NAT rules](/generalites/nat).
|
||||
- We assume you have the subdomain `films.mydomain.com` with a `CNAME` pointing to `films.fr` in your [DNS zone](/general/dns). And that [unless you’re using Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` on your router is forwarded to port `443` on your server via [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
|
||||
@@ -40,7 +40,7 @@ Configure the `.env` file by copying the latest version [from here](https://gith
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- If you're using a NAS or a network-shared drive via [Samba](/generalites/samba/) to store your data, replace the value of `UPLOAD_LOCATION`{lang=properties} with the path to your shared folder.
|
||||
- If you're using a NAS or a network-shared drive via [Samba](/general/samba/) to store your data, replace the value of `UPLOAD_LOCATION`{lang=properties} with the path to your shared folder.
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -59,7 +59,7 @@ The main benefit of this setup is being able to access Immich remotely on all yo
|
||||
::alert{type="info"}
|
||||
📋 __Before you begin:__
|
||||
<br/><br/>
|
||||
We assume that you have a subdomain `immich.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/generalites/dns). Also, unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare), make sure port `443` on your router is forwarded to port `443` on your server via [NAT rules](/generalites/nat).
|
||||
We assume that you have a subdomain `immich.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/general/dns). Also, unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare), make sure port `443` on your router is forwarded to port `443` on your server via [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
In Dockge, open the SWAG stack and edit the compose file to add Immich's network:
|
||||
|
||||
@@ -57,7 +57,7 @@ services:
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- If you’re using a NAS or network-shared drive via [Samba](/generalites/samba), replace `/docker/nextcloud/data` with the path to your shared folder.
|
||||
- If you’re using a NAS or network-shared drive via [Samba](/general/samba), replace `/docker/nextcloud/data` with the path to your shared folder.
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -89,7 +89,7 @@ The goal of this setup is to access Nextcloud remotely from all your devices. We
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- We assume you have a subdomain `nextcloud.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/generalites/dns). And unless you’re using [Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` on your router must be forwarded to port `443` on your server using [NAT rules](/generalites/nat).
|
||||
- We assume you have a subdomain `nextcloud.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/general/dns). And unless you’re using [Cloudflare Zero Trust](/serveex/securite/cloudflare), port `443` on your router must be forwarded to port `443` on your server using [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
|
||||
@@ -67,7 +67,7 @@ You may want to access File Browser remotely from all your devices. To do that,
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- __Pre-requisite:__ We assume you've already created a subdomain like `files.yourdomain.com` in your [DNS zone](/generalites/dns) pointing to `yourdomain.com` with a `CNAME`, and—unless you're using Cloudflare Zero Trust—have already forwarded port `443` on your router to port `443` on your server using [NAT rules](/generalites/nat).
|
||||
- __Pre-requisite:__ We assume you've already created a subdomain like `files.yourdomain.com` in your [DNS zone](/general/dns) pointing to `yourdomain.com` with a `CNAME`, and—unless you're using Cloudflare Zero Trust—have already forwarded port `443` on your router to port `443` on your server using [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -160,5 +160,5 @@ Press `Esc`, then save and exit with `:x` followed by `Enter`.
|
||||
That’s it—File Browser is now exposed!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `files.subdomain.conf` and uncommenting `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `files.subdomain.conf` and uncommenting `include /config/nginx/authentik-server.conf;`{lang=nginx} and `include /config/nginx/authentik-location.conf;`{lang=nginx}. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
@@ -81,7 +81,7 @@ Tout l'intérêt d'une telle solution, c'est de pouvoir y accéder à distance e
|
||||
::alert{type="info"}
|
||||
📋 __Au préalable :__
|
||||
<br/><br/>
|
||||
Nous partons du principe que vous avez le sous-domaine `pingvin.mondomaine.fr` avec un `CNAME` qui pointe vers `mondomaine.fr` dans votre [zone DNS](/generalites/dns). Et que bien sûr, [à moins que vous utilisiez Cloudflare Zero Trust](/serveex/securite/cloudflare), le port `443` de votre box pointe bien sur le port `443` de votre serveur via [les règles NAT](/generalites/nat).
|
||||
Nous partons du principe que vous avez le sous-domaine `pingvin.mondomaine.fr` avec un `CNAME` qui pointe vers `mondomaine.fr` dans votre [zone DNS](/general/dns). Et que bien sûr, [à moins que vous utilisiez Cloudflare Zero Trust](/serveex/securite/cloudflare), le port `443` de votre box pointe bien sur le port `443` de votre serveur via [les règles NAT](/general/nat).
|
||||
::
|
||||
|
||||
Dans Dockge, rendez-vous dans la stack de SWAG et éditez le compose en ajoutant le réseau de pingvin :
|
||||
|
||||
@@ -122,7 +122,7 @@ The whole point of such a solution is to access it remotely from any device. To
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- __Preliminary:__ We assume you’ve created a subdomain like `code.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/generalites/dns), and—unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare)—that you’ve forwarded port `443` from your router to port `443` on your server using [NAT rules](/generalites/nat).
|
||||
- __Preliminary:__ We assume you’ve created a subdomain like `code.yourdomain.com` with a `CNAME` pointing to `yourdomain.com` in your [DNS zone](/general/dns), and—unless you're using [Cloudflare Zero Trust](/serveex/securite/cloudflare)—that you’ve forwarded port `443` from your router to port `443` on your server using [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -219,5 +219,5 @@ Press `Esc`, then save and exit by typing `:x` and pressing `Enter`.
|
||||
That’s it — code-server is now exposed!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `code.subdomain.conf` and uncommenting the lines `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `code.subdomain.conf` and uncommenting the lines `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
@@ -74,7 +74,7 @@ The benefit of this setup is being able to access it remotely from any of your d
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- __Prerequisite:__ We assume you have created a subdomain such as `gitea.yourdomain.com` in your [DNS zone](/generalites/dns) with `CNAME` pointing to `yourdomain.com`, and [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), you have already forwarded port `443` from your router to your server’s port `443` in the [NAT rules](/generalites/nat).
|
||||
- __Prerequisite:__ We assume you have created a subdomain such as `gitea.yourdomain.com` in your [DNS zone](/general/dns) with `CNAME` pointing to `yourdomain.com`, and [unless you're using Cloudflare Zero Trust](/serveex/securite/cloudflare), you have already forwarded port `443` from your router to your server’s port `443` in the [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
|
||||
@@ -58,7 +58,7 @@ You might want to access it remotely on all your devices. To do that, we'll expo
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- __Pre-requisite:__ We assume you’ve created a subdomain like `tools.yourdomain.com` in your [DNS zone](/generalites/dns) with `CNAME` set to `yourdomain.com`. Also, unless you’re using [Cloudflare Zero Trust](/serveex/securite/cloudflare), make sure you’ve already forwarded port `443` from your router to port `443` on your server in the [NAT rules](/generalites/nat).
|
||||
- __Pre-requisite:__ We assume you’ve created a subdomain like `tools.yourdomain.com` in your [DNS zone](/general/dns) with `CNAME` set to `yourdomain.com`. Also, unless you’re using [Cloudflare Zero Trust](/serveex/securite/cloudflare), make sure you’ve already forwarded port `443` from your router to port `443` on your server in the [NAT rules](/general/nat).
|
||||
:::
|
||||
::
|
||||
|
||||
@@ -162,5 +162,5 @@ Press `Esc`, then save and exit by typing `:x` and pressing `Enter`.
|
||||
And that’s it — IT Tools is now exposed!
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__ You can secure this app with Authentik by opening `tools.subdomain.conf` and uncommenting the lines `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and a provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ __Tip:__ You can secure this app with Authentik by opening `tools.subdomain.conf` and uncommenting the lines `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don’t forget to [create an application and a provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
@@ -104,7 +104,7 @@ To make AdGuard usable from outside your home network, you need to expose it.
|
||||
|
||||
::alert{type="info"}
|
||||
:::list{type="info"}
|
||||
- __Prerequisites:__ We assume you've created a subdomain like `adguard.mydomain.com` in your [DNS zone](/generalites/dns) with a `CNAME` pointing to `mydomain.com`, and that you’ve already forwarded port `443` from your router to port `443` on your server in your [NAT rules](/generalites/nat). Also forward port `53` and port `853` to your server. These ports are used to route DNS requests.
|
||||
- __Prerequisites:__ We assume you've created a subdomain like `adguard.mydomain.com` in your [DNS zone](/general/dns) with a `CNAME` pointing to `mydomain.com`, and that you’ve already forwarded port `443` from your router to port `443` on your server in your [NAT rules](/general/nat). Also forward port `53` and port `853` to your server. These ports are used to route DNS requests.
|
||||
:::
|
||||
::
|
||||
|
||||
|
||||
@@ -105,10 +105,10 @@ Recently, Vaultwarden requires SSL to be accessed, which prevents access via a l
|
||||
|
||||
## Exposing Vaultwarden with SWAG
|
||||
---
|
||||
The main benefit of Vaultwarden is being able to access it remotely from any device. We'll expose it through [SWAG](/serveex/coeur/swag).
|
||||
The main benefit of Vaultwarden is being able to access it remotely from any device. We'll expose it through [SWAG](/serveex/core/swag).
|
||||
|
||||
::alert{type="info"}
|
||||
✨ __Before you start:__ Make sure you've created a DNS subdomain like `vault.yourdomain.com` with `CNAME` pointing to `yourdomain.com` and (unless using Cloudflare Zero Trust) that you've forwarded port `443` from your router to your server's `443` via [NAT rules](/generalites/nat).
|
||||
✨ __Before you start:__ Make sure you've created a DNS subdomain like `vault.yourdomain.com` with `CNAME` pointing to `yourdomain.com` and (unless using Cloudflare Zero Trust) that you've forwarded port `443` from your router to your server's `443` via [NAT rules](/general/nat).
|
||||
::
|
||||
|
||||
In Dockge, go to the SWAG stack and edit the compose file to add the Vaultwarden network:
|
||||
@@ -240,5 +240,5 @@ And there you go — Vaultwarden is now exposed! Visit `vault.yourdomain.com` to
|
||||
Don't forget to install Bitwarden browser extensions (they work with Vaultwarden) for [Chrome](https://chromewebstore.google.com/detail/gestionnaire-de-mots-de-p/nngceckbapebfimnlniiiahkandclblb) and [Firefox](https://addons.mozilla.org/fr/firefox/addon/bitwarden-password-manager/), as well as [iOS](https://apps.apple.com/fr/app/bitwarden/id1137397744) and [Android](https://play.google.com/store/apps/details?id=com.x8bit.bitwarden&hl=fr) apps to sync your passwords.
|
||||
|
||||
::alert{type="success"}
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `tools.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don't forget to [create an application and provider in Authentik](/serveex/securite/authentik#protéger-une-app-par-reverse-proxy).
|
||||
✨ __Tip:__ You can protect this app with Authentik by opening `tools.subdomain.conf` and removing the `#` in front of `include /config/nginx/authentik-server.conf;` and `include /config/nginx/authentik-location.conf;`. Don't forget to [create an application and provider in Authentik](/serveex/securite/authentik#protecting-an-app-via-reverse-proxy).
|
||||
::
|
||||
Reference in New Issue
Block a user